Google has detailed its work discovering a new Rowhammer vulnerability dubbed "Half-Double", which evolves the style of attack on DRAM memory first reported in 2014 and suggests the Rowhammer problem won't go away soon.
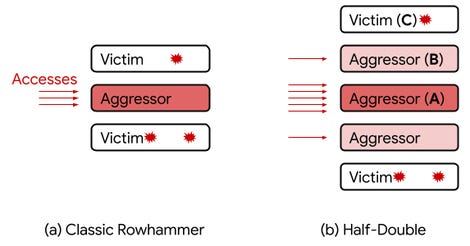
The Rowhammer attack is unusual because it aims to cause "bit flips" by rapidly and repeatedly accessing data in one memory row on a RAM chip to create an electrical charge that changes data stored in other addresses in an adjacent "memory row" on a chip. The attacking memory rows are called "aggressors" and the rows where bit flips occur are called "victim rows".
Over the years since the first Rowhammer attack was discovered, researchers have demonstrated numerous ways to use the technique to alter data stored on RAM cards, including DDR3 and DDR4 generations.
While initially limited to scenarios where an attacker had physical access to the target, researchers eventually showed a Rowhammer attack could be carried out remotely over the web and use the technique to gain control of Linux VMs in the cloud.
As Google Project Zero (GPZ) researchers explained in 2015, Rowhammer attackers work because DRAM cells are gradually becoming smaller and closer together. Miniaturization and the ability to pack in more memory capacity has made it harder to prevent DRAM cells from interacting electrically with each other.
"Accessing one location in memory can disturb neighboring locations, causing charge to leak into or out of neighboring cells. With enough accesses, this can change a cell's value from 1 to 0 or vice versa," GPZ researchers explained of bit flips.
The Half-Double, which Google details on a PDF on GitHub, "capitalizes on the worsening physics of some of the newer DRAM chips to alter the contents of memory," Google researchers explain in a new blogpost.
The style of attack is comparable to the speculative execution attacks on CPUs (Spectre and Meltdown), but rather focus on design vulnerabilities in DRAM. The consequences can be pretty nasty if the attacker successfully exploits these design issues.
"As an electrical coupling phenomenon within the silicon itself, Rowhammer allows the potential bypass of hardware and software memory protection policies. This can allow untrusted code to break out of its sandbox and take full control of the system," write Google's research team, which includes Salman Qazi, Yoongu Kim, Nicolas Boichat, Eric Shiu & Mattias Nissler.
Kim, now a software engineer at Google, was one of the researchers who reported the first Rowhammer vulnerability.
The Half-Double expands the original Rowhammer attack, which could cause bit flips at a distance of one DRAM row. The Half-Double shows the aggressor rows can cause bit flips on more distant victim rows.
"With Half-Double, we have observed Rowhammer effects propagating to rows beyond adjacent neighbors, albeit at a reduced strength," the team notes.
"Given three consecutive rows A, B, and C, we were able to attack C by directing a very large number of accesses to A, along with just a handful (~dozens) to B. Based on our experiments, accesses to B have a non-linear gating effect, in which they appear to "transport" the Rowhammer effect of A onto C."
The Half-Double is interesting because it's a property of the underlying silicon substrate, and suggests the increasing density of cells means Rowhammer vulnerabilities will live on. They add that Half-Double also differs from the TRRespass attack on DDR4 RAM detailed in 2020, which relied on reverse engineering to undermine some of the Rowhammer mitigations that DRAM vendors had implemented to prevent these attacks in DDR4.
"This is likely an indication that the electrical coupling responsible for Rowhammer is a property of distance, effectively becoming stronger and longer-ranged as cell geometries shrink down. Distances greater than two are conceivable," the researchers note.
Google additionally has been working with the semiconductor engineering trade organization JEDEC to search for mitigations to Rowhammer.
May 26, 2021 at 08:57PM
https://ift.tt/3hT7tR9
This weird memory chip vulnerability is even worse than we realised - ZDNet
https://ift.tt/2RGyUAH
Chips

No comments:
Post a Comment